How To Ensure Your Crypto Is Safe & Secure In Your Wallet

Cyber Security is of enormous importance in this modern age. Ensuring the safety of your personal information, account passwords, and digital assets is crucial — especially with the significant rise in cybercrime over the last decade.
According to Accenture, security breaches have skyrocketed by 67% over the last 5 years.
Cybercriminals are using many malicious tools, such as malware, ransomware, and viruses, to target individuals. But these malicious tools aren't just designed to access your sensitive information. As the popularity of cryptocurrency has risen dramatically over the last few years, cyberattacks on cryptocurrency holders have also increased. Many reputable cryptocurrency exchanges, including Binance, have also been the victim of security breaches.
Some crypto users have also become victims of fake cryptocurrency wallets — having their holdings stolen as soon as they transfer them. Keeping your crypto and other digital assets safe is imperative. In this article, we're going to provide you with a list of tips to improve your cybersecurity — keeping your crypto portfolio safe from cybercriminals.
Tips On Keeping Your Crypto Wallet Secure:
Keep Your Private Key & Recovery Phrase Safe:
This may seem obvious, but ensuring that your crypto wallet’s private key and recovery phrase are kept safe is crucial. To do this, you want to keep multiple copies of both your private key and recovery phrase. The best way to do this would be to write your private key and recovery phrase on a sheet of paper and keep them hidden somewhere secure. Keeping an offline backup of your wallet keys and recovery phrases in a trust location is essential if you want to ensure the security of your crypto holdings.
Bonus tip: To further protect your private key and recovery phrase, you can split each into two or more pieces — storing them in separate locations. This is definitely something you should consider if you're going to store your sensitive data on a computer or online.
Consider Hardware Wallets
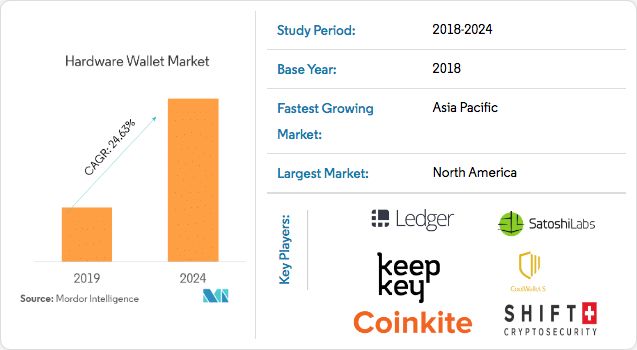
Also known as "cold storage", cryptocurrency hardware wallets enable you to store your cryptos and other digital assets offline securely. Hardware wallets are becoming increasingly popular amongst crypto enthusiasts looking to store their holdings offline securely — the market is expected to boom to nearly $500 million in 5 years.
You can easily connect USB hardware wallets to your computer — where you can safely manage your crypto holdings. You will be able to send crypto to your hardware wallet's address directly from your current wallet.
We recommend storing larger amounts of crypto on a hardware wallet and only keeping small amounts on your online wallet for day-to-day use. There are many hardware wallet solutions available on the market. The most notable brands include Ledger and Trezor.
Use Two-Factor Authentication
Two-factor authentication (2FA) is one of the best ways to ensure the safety of your crypto wallet. 2FA offers an extra layer of password security to your crypto wallet. Many popular wallets offer two-factor authentication as standard — you can easily set this up in your account settings. You'll be able to connect your crypto wallet account with a 2FA app such as Google Authenticator. The app will generate time-based one-time passwords, refreshing every 30 seconds.
Alternatively, many wallet providers will give you the ability to receive SMS or email alerts, providing you with a specific code every time you want to log into your account — keeping you one step ahead of hackers.
Never Store Your Details Online
This goes without saying — storing your private keys or your recovery phrase online could be a bad decision. Notable crypto investors have reportedly had their holdings stolen due to storing their wallet details online. Storing your private wallet data online can leave you vulnerable to having your wallet access by cybercriminals. Avoid saving your sensitive data on emails, social network sites, or note-keeping platforms such as Evernote.
If you must store your details online, it's best to follow our advice above — split your data into multiple pieces and store each piece in a different location. Even if cybercriminals can gain access to one part of your data, they won't be able to access your crypto wallet without all the pieces of your private key or recovery phrase.
Use VPNs When Logging In
This point is extremely important if you’re traveling to different locations — away from your home network — and decide to use public Wi-Fi. We strongly recommend using a reputable VPN service if you’re going to access your online crypto wallet using a public Wi-Fi connection. Free internet connections are notorious for having cybercriminals breach the network, gaining access to sensitive information from all individuals using the network.
This is why using a trust VPN provider, is imperative when access your crypto holdings using public internet connections.
Installing Antivirus Software
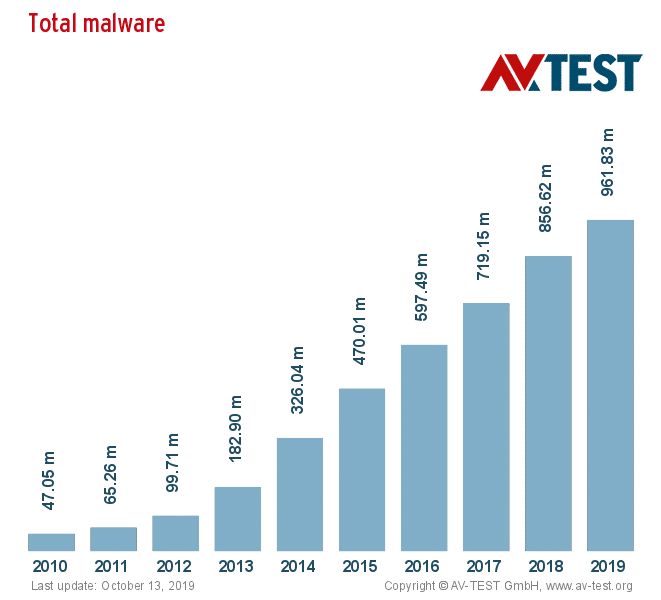
(Source)
Antivirus software providers, such as Norton, will equip you will all the essential cybersecurity tools. This will enable you to secure all of the information stored locally on your device and help you protect your device from cryptojacking. Most antivirus software providers will also have integrated web protection — using advanced AI and machine learning techniques to detect potential threats, such as malware and phishing attacks — helping to protect all of your sensitive information from hackers.
Using antivirus software eliminates the threat posed by online criminals when you’re logging into — and using — your online crypto wallet.
Always Download A Trusted Wallet
With the rise in fake cryptocurrency wallets and apps, it’s more important than ever to ensure you’ve downloaded a trusted wallet. Always double-check the developers behind your chosen wallet — even if the wallet or app is available on a reputable app store such as Google Play or the App Store. CoinSpace, provides a collection of trusted, verified cryptocurrency wallets to store Bitcoin, Ethereum, Litecoin, and more.
Conclusion
You can be faced with many cybersecurity risks — especially when you’re storing your cryptocurrency and crypto wallet data online. Using the tips in this article will help you to significantly increase your cybersecurity measures, reducing the risks posed by crypto wallet hackers and other cybercriminals. Being proactive is the key to great cybersecurity. By using a combination of the practices outlined above — especially cold storage, two-factor authentication, and antivirus software — you will be able to securely store and transact your crypto without having to worry about becoming a victim of cybercrime.
Feature image by Moja Msanii on Unsplash